At a recent meeting of lawyers at a local bar association, the topic of discussion was cyber and information security.
For Attorneys, Knowing the Difference Between Structured and Unstructured Data is Crucial
Topics: Structured Data, Legal Technology, Data Security, Ethics, unstructured data
In “When Key Employees Quit: 5 Things You Must Do to Keep Control of Critical Data,” Michael Ciaramitaro and Sarah Brown, both of Inventus, point out the number one vulnerability for most companies: “Organizations today rely heavily upon technology and electronically stored information – and when employees leave, there’s always a risk that they’ll take some information or data with them when they go, either inadvertently or on purpose.”
Topics: risk management, Differential Sharing, information security, unstructured data
In her 6/26/19 article for Legal Tech News, “Can Cloud Providers Calm Legal’s Apprehensions,” Victoria Hudgins, observes: “As cloud computing becomes more popular, some law firms and corporate legal departments aren’t jumping fully on the bandwagon.”
Topics: LegalTechnology, databreach, sensitive data, Differential Sharing, Data Security, cloud computing, unstructured data
“General Counsel Thirsty for Learning Better Methods of Cybersecurity Compliance Programs”
Sue Reisinger reported in Corporate Counsel that, “As Cyberattacks on Business Grow, General Counsel Are 'Thirsty' for More Details.” This is great news! When a profession is thirsty for details – for knowledge - solutions follow, and in the typhoon of cybercrime happening today, thirst for solutions is exactly what is needed.
Topics: compliance, cybersecurity, General Counsel, Legal Technology, cybercrime, corporatelegal
Today, security is top of mind for many in the legal profession. The EU’s GDPR, now one-year-old, certainly grabbed our attention and California’s similar CPPA, set to take effect early next year, has increased awareness. While the news has extensively covered major data breaches, it is easy for lawyers, law firms, in-house counsel, and their staffs to dismiss exposure to those occurrences because we typically do not collect large volumes of data in our day-to-day practices.
Topics: LegalTech, sensitive information, Court Documents, GDPR, Cyber Security, Legal Technology, Data Security, Ethics
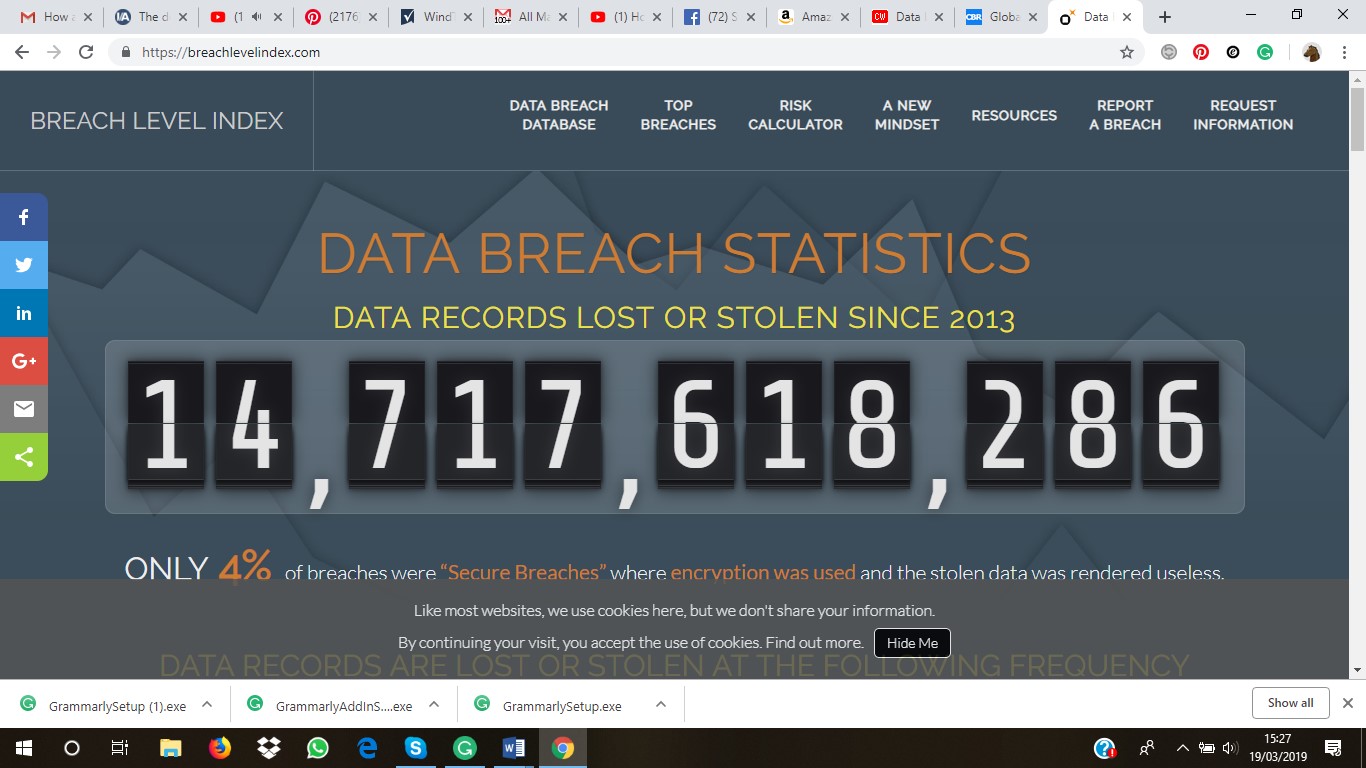
In his 3/8/17 article, “Rising cost of data breaches to $2.1 trillion by 2019…” Luke Irwin of IT Governance ominously wrote: “[We] found an astounding figure of 3.1 billion records leaked in 2016, conservatively. We also discovered an infiltration of law firms’ email worth $4 million stolen [and] data breaches anticipated to be at 2.1 trillion by 2019, in less than 2 years from now.”
Topics: LegalTech, compliance, databreach, Unstructureddata, Cyber Security, Legal Technology, Data Security, Luke Irwin, Global Breach Level Index
GDPR: American Progress in Privacy Protection with Implications for Attorney Cyber-Info-Security
Despite some discernible progress in privacy protection since the European Union's General Data Protection Regulation (GDPR) was enacted one year ago, in America it’s practically non-existent. In a Microsoft blog post, Corporate VP & Deputy General Counsel, Julie Brill recounted the progress that has been made since GDPR’s adoption, concluding with a predictable call for further progress to be made in the year to come, including adoption of uniform federal legislation similar to the EU GDPR.
Topics: cybersecurity, GDPR, Microsoft Privacy Platform, Microsoft, Cyber Security, law firms, Privacy Protection, information security
Misery loves company, you could say, but when you are the guardian at the gate, this may be company you don’t want to keep. In “Highlights of Verizon’s 2019 Data Breach Investigations Report,” Sharon Nelson, takes on and highlights Verizon’s most recent survey. In short, the news is not good for anyone in general, and professionals in particular.
Topics: security, risk management, LegalIT, legaltecheducation, Differential Sharing, DBIR, Structured Data, Verizon Data Breach Investigations Report
Time for Courts and the Legal Profession to Jointly Adopt State-of-the-Art Infosecurity Solutions
The noted authority, Sharon D. Nelson, Esq., recently reported in her Ride the Lightning Blog: “Bank Sued Over Court Filing Containing Lawyers’ Personal Information,” a thorny bank litigation case that serves to highlight the critical importance of courts and litigators coming together to jointly adopt state-of-the-art infosecurity software and protocols.
Topics: Differentialsharing, compliance, cybersecurity, softwaresolutions, sensitive data, infosecurity, Differential Sharing, Court Documents
In an article by Victoria Hudgins, writing for LegalTechNews.com, “Sink or Swim: Law Firms Need to Leverage, Understand Tech to Survive,” stated, “For law firms and their in-house partners to survive and thrive, differentiating services and analyzing big data will be key, while understanding and harnessing technology are the first big steps, according to a Wolters Kluwer survey.”
Topics: LegalTechnology, Differentialsharing, LegalTech, cybersecurity, General Counsel, LegalIT, adaptation, legaltecheducation